What is Ransomware ?
Ransomware is a type of malicious software (malware) that encrypts your files or locks your systems, preventing access until a ransom is paid. Cybercriminals typically demand payment in cryptocurrency to restore access. Unfortunately, ransomware attacks have become increasingly sophisticated and harder to combat.
Ransomware attacks have quickly become a growing nightmare for both businesses and individuals. Imagine this: one day, you try to access your files, only to discover that everything is locked. Suddenly, a threatening message appears, demanding payment in exchange for your data. In such a situation, what would you do? Should you consider paying the ransom? Let’s explore this pressing issue in greater detail.
Types of Ransomware
Ransomware comes in various forms, each with its own methods and impact. Here are the most common types:
- Crypto Ransomware
This type encrypts your files, making them inaccessible without a decryption key. It’s one of the most common and devastating types.
Example: The WannaCry attack in 2017 affected over 200,000 computers worldwide, demanding ransom payments in Bitcoin. - Locker Ransomware
Unlike crypto ransomware, locker ransomware locks you out of your entire device rather than specific files. You’ll often see a ransom note displayed on your screen.
Example: The Reveton ransomware pretended to be a message from law enforcement, demanding payment for alleged illegal activity. - Scareware
Scareware uses fake warnings and alerts to trick users into paying a ransom. It may claim your system is infected and demand payment to “fix” the issue.
Example: Rogue antivirus software that locks the screen until a “subscription” fee is paid. - Ransomware-as-a-Service (RaaS)
This is a business model where cybercriminals offer ransomware tools to others in exchange for a cut of the ransom profits. It has made launching attacks easier for even non-technical criminals.
Example: The GandCrab ransomware was offered as a service, earning millions of dollars for its operators. - Double Extortion Ransomware
This modern twist not only encrypts files but also steals sensitive data. Attackers threaten to leak the information if the ransom isn’t paid.
Example: The Maze ransomware group pioneered this method, targeting organizations worldwide. - Mobile Ransomware
This targets smartphones and tablets, often spreading through malicious apps. It locks the device or encrypts files, demanding payment for access.
Example: The SLocker ransomware mimicked law enforcement agencies to extort money from victims.
Real-Life Scenarios of Ransomware Attacks
I will walk you through with couple real life examples of how hackers execute this type of attacks,

- 1. Spear Phishing Email
A hospital employee receives an email claiming to be from a trusted vendor. The email contains a legitimate-looking invoice attachment. Upon opening the attachment, malicious code executes, encrypting patient records and critical systems. The attackers demand a $500,000 ransom in Bitcoin to restore access.
Example: The 2017 ransomware attack on the National Health Service (NHS) in the UK started with phishing emails and caused widespread disruptions.
- 2. Exploiting Un-patched Software
A company fails to update its server software, leaving it vulnerable to known exploits. Attackers use this vulnerability to infiltrate the network, deploy ransomware, and lock down operational systems. Employees are greeted with a ransom note demanding payment to decrypt essential files.
- Example: The WannaCry ransomware exploited the EternalBlue vulnerability in outdated Windows systems, crippling organizations worldwide.
How to Navigate Ransomware Demands & Negotiations
| One of the most significant dangers facing businesses today is the ever-present threat of a ransomware attack. In these attacks, hackers use ransomware to encrypt critical data, effectively locking companies out of their own systems. As a result, operations can grind to a halt, and in some cases, this disruption has even forced businesses to shut down permanently. Given these high stakes, many companies find themselves grappling with a difficult decision: should they pay the ransom to recover their data, or are there better alternatives? In most cases, the answer is no. Businesses should avoid paying the ransom unless they have exhausted all other options for survival. In this post, we’ll delve into the reasons why. |
What the FBI Says About Paying the Ransom
In its Ransomware Prevention guide, the FBI warns, “The United States Government (USG) does not encourage paying a ransom to criminal actors” and doing so comes with “serious risks.
The Dilemma: To Pay or Not to Pay?
| When hit by ransomware, organizations face a tough decision. Here are the key arguments for both sides: Why Some Choose to Pay Business Continuity: For critical operations, time is money. Downtime can cost millions of dollars per day. Example: In 2020, a German hospital paid a ransom after patient care systems were disrupted. Lack of Backups: Without a proper backup strategy, paying may seem like the only way to recover data. Pressure to Protect Sensitive Data: If attackers threaten to leak sensitive information, companies may pay to avoid reputational damage. Why Experts Advise Against Paying No Guarantees: There’s no assurance that paying will actually restore your data. Example: A Florida city paid $600,000 in ransom but still struggled to recover all their files. Encourages Cybercrime: Paying a ransom funds attackers and motivates them to target others. Risk of Repeat Attacks: Once you pay, you may be marked as an easy target for future attacks. |
Alternatives to Paying
- Restore from Backups: Always maintain up-to-date backups stored offline. This is your strongest defense.
- Engage Cybersecurity Experts: Professionals can help with decryption tools or secure recovery.
- Inform Law Enforcement: Report the attack to local authorities or organizations like the FBI.
- Improve Cybersecurity: Prevention is better than cure. Invest in strong firewalls, employee training, and regular updates.
Legal and Ethical Considerations
In some countries, paying ransom might be illegal, especially if the attackers are linked to sanctioned groups. Ethically, paying could make you complicit in fueling cybercrime.
Real-Life Success Without Paying
Many organizations have stood firm and refused to pay. In 2019, the city of Baltimore was hit by ransomware but chose not to pay the $76,000 ransom. While recovery was costly, they sent a clear message to attackers.
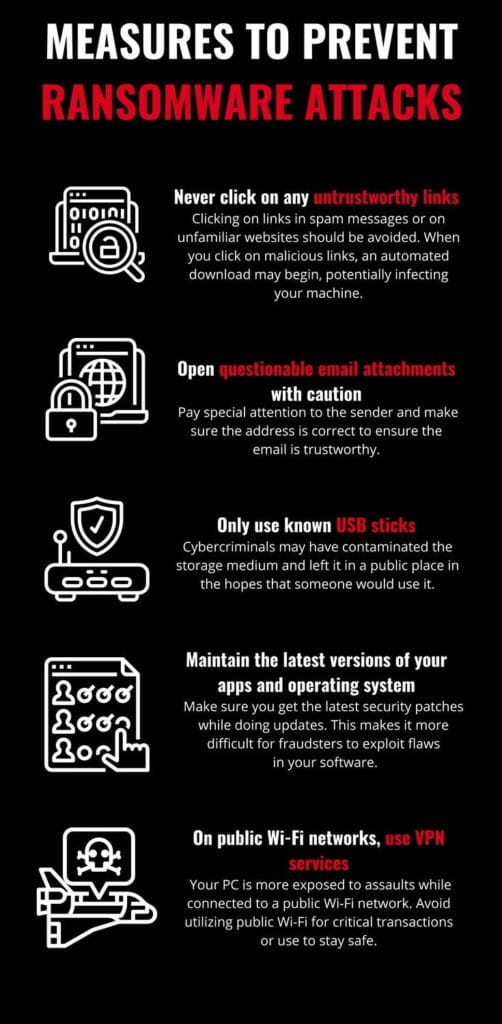
Best Practices to Prevent Ransomware
1. Regular Backups
- Frequent Backups: Regularly back up critical data to offline or cloud storage. Make sure backups are not directly accessible from your network.
- Test Backups: Periodically verify the integrity and accessibility of your backups to ensure they can be restored quickly.
2. Use Reliable Security Software
- Anti-Ransomware Tools: Employ reputable anti-malware and anti-ransomware tools that offer real-time protection.
- Regular Scans: Schedule regular system scans to detect potential threats.
- Automatic Updates: Ensure that your security software is configured to receive automatic updates for the latest definitions.
3. System and Software Updates
- Patch Management: Always apply software patches and updates for your operating system and applications as soon as they are available. Many ransomware attacks exploit known vulnerabilities.
- Enable Auto-Updates: Whenever possible, enable automatic updates for software and operating systems.
4. Email Security
- Be Wary of Phishing: Avoid clicking on suspicious links or downloading attachments from unknown or untrusted email addresses. Phishing is a common attack vector for ransomware.
- Advanced Email Filtering: Use advanced spam filters and email security gateways to block malicious emails before they reach your inbox.
- Educate Users: Train yourself and others in your organization on how to identify phishing emails.
5. Network Segmentation
- Limit Lateral Movement: Use network segmentation to limit the spread of ransomware in case of a breach. Separate critical infrastructure and sensitive data from less important systems.
- Restrict Remote Desktop Protocol (RDP): If RDP is not needed, disable it. Otherwise, ensure strong authentication and encryption are used.
6. Access Control
- Least Privilege Principle: Only give users access to the resources and systems they absolutely need. Limit administrative privileges.
- Multi-Factor Authentication (MFA): Implement MFA to add an additional layer of security, especially for remote access and administrative accounts.
7. Network Security
- Firewalls: Use firewalls to block access to known malicious IPs and prevent unauthorized inbound and outbound network traffic.
- VPN: Use a Virtual Private Network (VPN) when accessing sensitive resources remotely, especially over public networks.
8. Ransomware Detection Tools
- Behavioral Analysis Tools: Employ tools that detect ransomware based on behavior, such as unusual file modifications or encryption patterns.
- File Integrity Monitoring: Use file integrity monitoring tools to alert you to unexpected changes in critical files.
9. Disable Macros and Scripting
- Disable Macros: Disable macros in office documents by default, as they are a common method for delivering ransomware.
- Restrict Scripting: Avoid unnecessary scripts running on your systems to reduce the attack surface.
10. Incident Response Plan
- Create a Response Plan: Develop and regularly update an incident response plan to quickly respond to a ransomware attack.
- Test the Plan: Periodically test your response plan to ensure that all stakeholders know their roles in case of an attack.
11. Avoid Paying Ransom
- Do Not Pay Ransom: Paying the ransom does not guarantee recovery of your data and encourages further attacks. Law enforcement agencies generally advise against paying the ransom.
12. Educate and Train Employees
- Security Awareness Training: If you’re an organization, ensure all employees are educated about safe online practices and how to spot phishing attempts, avoid suspicious links, and safely handle attachments.
Conclusion
When it comes to ransomware, prevention is your best defense. Paying the ransom might seem like a quick fix, but it’s rarely the right solution. By strengthening cybersecurity measures and planning ahead, you can reduce your risk and avoid supporting cybercriminals.
In the end, the choice to pay or not comes with heavy consequences. Think carefully and consult experts before making any decision. Remember, your data’s safety begins with preparation.


