What is Cryptographic Failures to start with ?
Consider a locked chest meant to safeguard your valuables.

Now, if the lock itself is broken or poorly designed, it becomes easy for someone to access what’s inside. That’s precisely how cryptographic failures work in the digital world.
Cryptographic failures occur when the tools used to encrypt and protect sensitive data are flawed or misused. This can expose this information, like passwords, credit card details, and other confidential data, to unauthorized access, changes, or theft.
Before delving into the topic further, it’s essential to understand couple of fundamental concepts:
1. Encryption
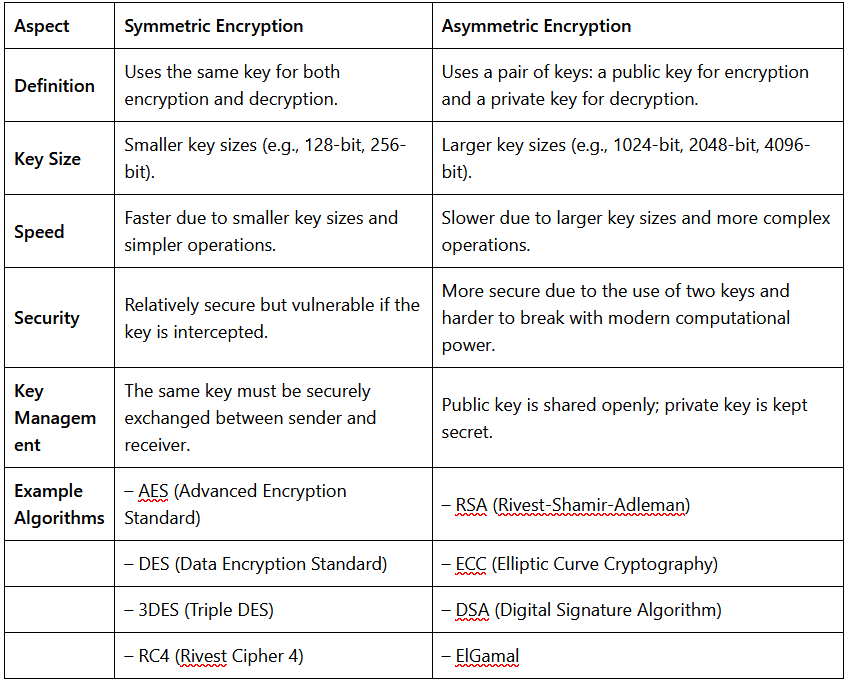
Encryption is a process of converting plaintext or data into ciphertext using an algorithm and a key. This ciphertext can only be decrypted back to its original form by someone who possesses the corresponding decryption key.It is primarily used to maintain the confidentiality of the data.
Encryption Algorithms :
2. Hashing
Hashing plays a crucial role in cryptography and computer science. It involves transforming input data of any size into a fixed-size string of characters using a hashing algorithm. The algorithm computes a hash value or hash code, which serves as a unique representation of the original input data.
Strong hashing algorithms, such as SHA-256, play a crucial role in various applications like digital signatures, password storage, and data verification.These algorithms generate hash values that are highly secure and nearly impossible to reverse engineer back to the original input. As a result, they provide cryptographic security and ensure data integrity.
Conversely, weak hashing algorithms like MD5 and SHA1 contain known vulnerabilities and require avoidance in secure applications. Attackers can easily compromise these algorithms through brute-force attacks or collisions, where different inputs generate the same hash value. For this reason, avoid using weak hashing algorithms to protect sensitive data.
In conclusion, hashing plays a vital role in data security by efficiently verifying information integrity. By opting for strong hashing algorithms like SHA-256 and avoiding weak ones like MD5 and SHA1, individuals and organizations can protect their data from unauthorized access and malicious actors.
Below are the some scenarios that depicts the Cryptographic Failures in a E-commerce platform.
1. Weak Encryption Algorithm
An e-commerce website uses an outdated algorithm like MD5 to store customer passwords. Consequently, attackers can easily crack MD5 hashes with available tools, gaining access to customer accounts and leading to unauthorized purchases and identity theft.
2. Insecure Key Management
An e-commerce website stores encryption keys on the server without proper security measures. As a result, hackers gain access to the server and steal the keys, enabling them to decrypt sensitive information, such as credit card details.
3. Data Transmission in Cleartext
An e-commerce website’s checkout form transmits customer payment information over an unencrypted connection (HTTP instead of HTTPS). This leaves the data vulnerable to Man-in-the-Middle attacks, where attackers intercept the communication to steal unencrypted data for fraudulent purposes.
4. Vulnerable Third-Party Library
An e-commerce website uses a third-party library for encryption functions but fails to update it regularly. Consequently, attackers exploit a known vulnerability in the library, allowing them to decrypt sensitive data stored on the website.
5. Improper Random Number Generation
The e-commerce website uses a predictable random number generator to create encryption keys. As a result, attackers exploit this predictability to guess the keys, decrypt sensitive data, and potentially compromise financial transactions.
By recognizing these common cryptographic failures, businesses can better protect sensitive customer information and mitigate security risks.
Strategies that can be applied to mitigate the risk of cryptographic failures.
- Use modern, strong encryption algorithms like AES and RSA with adequate key lengths.
- Securely manage cryptographic keys, including generation, storage, and rotation.
- Enforce secure communication channels like HTTPS/TLS for data in transit.
- Hash passwords securely using algorithms like SHA-256 with unique salts.
- Implement robust authentication and authorization mechanisms.
- Regularly audit and test cryptographic implementations for vulnerabilities.
- Stay updated on cryptographic best practices and emerging threats.
- Educate personnel on secure cryptographic practices and common pitfalls.
Top 10 interview questions on OWASP Top 10 Cryptographic Failures
1. What are cryptographic failures, and why are they critical in web application security?
Cryptographic failures occur when weak encryption techniques or improper key management expose sensitive data to attackers. Consequently, this can lead to data breaches, theft, or unauthorized access. Understanding these failures is crucial to ensure that sensitive information is protected in a secure manner.
2. How does weak encryption contribute to cryptographic failures in web applications?
Weak encryption algorithms, like MD5 or SHA1, are vulnerable to attacks. As a result, attackers can easily decrypt sensitive data. This highlights why it’s vital to use strong encryption methods such as AES to protect sensitive information.
3. What is the role of key management in preventing cryptographic failures?
Effective key management is essential to protect cryptographic keys from unauthorized access. Without proper security, attackers may steal or misuse these keys, compromising sensitive data. Therefore, encryption keys should be stored securely and rotated regularly.
4. How does improper key storage lead to cryptographic failures, and what are some best practices to mitigate this risk?
Storing encryption keys improperly, like on the server without encryption, makes them vulnerable to theft. Best practices, such as using hardware security modules (HSM) and environment variables, help manage and protect keys from unauthorized access.
5. Why is it important to transmit data over encrypted channels, and what risks does cleartext data transmission pose?
Transmitting sensitive information over unencrypted channels, like HTTP instead of HTTPS, exposes the data to interception. This leaves the data vulnerable to Man-in-the-Middle (MITM) attacks, where attackers can intercept and manipulate the communication.
6. What is the significance of using up-to-date cryptographic libraries, and how can outdated libraries lead to cryptographic failures?
Outdated cryptographic libraries often contain known vulnerabilities that attackers can exploit. Therefore, it is crucial to keep cryptographic libraries updated to ensure that they remain resistant to emerging threats.
7. How can improper random number generation compromise cryptographic systems?
Predictable random number generators (RNG) allow attackers to guess encryption keys or session tokens. This enables them to decrypt sensitive data. To prevent this, developers must use cryptographically secure RNGs to generate unpredictable keys and tokens.
8. Can you explain the concept of “padding oracle attacks” and their relevance to cryptographic failures?
Padding oracle attacks target weaknesses in padding schemes used in block ciphers. If attackers can determine whether a decrypted message is correctly padded, they can decrypt the entire ciphertext. To defend against this, developers should use modern ciphers like AES-GCM with authenticated encryption modes.
9. What are the risks associated with storing passwords using weak algorithms like MD5, and how can these be mitigated?
Storing passwords with weak algorithms like MD5 makes them susceptible to brute-force or rainbow table attacks. Using secure hashing algorithms such as bcrypt or Argon2, along with salt, can greatly reduce the likelihood of a successful attack.
10. What steps should developers take to secure sensitive data in transit and at rest?
To secure data in transit, developers should implement TLS/SSL encryption, ensuring that sensitive information remains protected during transmission. For data at rest, strong encryption algorithms, proper key management, and regular security audits are necessary to protect sensitive data from unauthorized access.
Read more about OWASP top 10: Here


